Connecting to little devices out in the real world, the ones that send us information or do things for us, feels like something from a movie, doesn't it? Well, it's actually happening all around us, and keeping those connections private and secure is a very big deal. Think about all the tiny computers, the "things" that make up the Internet of Things, or IoT as we often call it. These aren't just gadgets in your home; they are often out in the field, far from a desk, doing important work. Getting into them to check on things, fix something, or update their software needs a really good lock and key, you know, something that keeps out anyone who shouldn't be poking around.
When you're dealing with a system that lets you manage these far-off devices, like a remote IoT platform, making sure only the right people can talk to them is absolutely critical. It’s pretty much like having a secret handshake that only you and your trusted devices know. Without this kind of security, anyone could potentially listen in on what your devices are saying or, worse, tell them to do things they shouldn't. So, we look for simple, yet very strong ways to protect these digital conversations. It’s about making sure your smart systems stay smart and safe, and that, in a way, is what we're going to chat about today.
One of the best ways to keep these connections safe involves something called an SSH key. It sounds a bit technical, I guess, but it's really just a clever pair of digital keys that help your remote IoT platform talk securely to your devices. It’s a pretty neat system, actually, and it helps make sure that when you send a command or ask for information, it's truly you doing the asking, and nobody else. We'll go through what this means for you and your remote gadgets, just a little, and why it matters so much for peace of mind.
- Danielle Fishel Naked
- Joyce Dewitt
- Hisashi Ouchi Pictures
- Leo And Sagittarius Compatibility
- Listcrawler Arrest 2025
Table of Contents
- What's the Big Deal About an SSH Key for Your IoT Devices?
- Why Do We Even Need Secure Connections for Remote Devices?
- How Does a remoteiot platform ssh key Actually Work?
- Setting Up Your remoteiot platform ssh key - Is It Hard?
- What If Your remoteiot platform ssh key Doesn't Behave?
- The Good Stuff - What a remoteiot platform ssh key Brings You
- Looking Ahead - The Role of Your remoteiot platform ssh key
What's the Big Deal About an SSH Key for Your IoT Devices?
You might be wondering why a simple string of characters, what we call an SSH key, is so important for these small internet-connected devices. Well, think of it like this: your IoT devices are often out there, maybe in a factory, on a farm, or even inside your home, collecting information or performing tasks. They need to send this information back to a central place, your remote IoT platform, and sometimes you need to send instructions back to them. If these messages aren't protected, it's like sending a postcard with all your secrets written on it for anyone to read. That's why we need something more private, something that makes sure only the intended eyes see the messages and only authorized hands send the commands. It's pretty much a digital handshake that confirms identity, you know, before any actual conversation happens.
Getting to Know Your remoteiot platform ssh key
An SSH key, in its simplest form, is a pair of very long, unique codes. One part of the pair, called the public key, can be shared around. You put this public key on your IoT device. The other part, the private key, you keep super safe on your computer or, say, on your remote IoT platform. When you want to connect to a device, your platform sends a little message, and the device uses its public key to make sure it's really your platform talking. Then, your platform uses its private key to prove it's really you. It's a very clever system because the private key never leaves your control, so it’s much harder for someone to pretend to be you. This method provides a very strong layer of security, so, it's pretty much essential for any serious IoT setup. It helps keep things quiet and only between you and your devices, which is actually quite reassuring.
Why Do We Even Need Secure Connections for Remote Devices?
It's a fair question, isn't it? Why go through the extra step for these tiny machines? Imagine a smart thermostat in your house. If someone could just hop in and change its settings, that's not ideal, but probably not the end of the world. Now, think about a sensor in a critical piece of industrial equipment, or a device that manages water flow in a city. If those connections aren't secure, bad actors could mess with vital services, steal important data, or even cause physical damage. It's a bit like leaving the front door of your house wide open for anyone to walk in. We want to prevent unauthorized access, data snooping, and malicious control. So, securing every point of connection, especially with devices that are often out of sight, is really quite important for peace of mind, obviously.
Keeping Your remoteiot platform ssh key Safe
The SSH key system is a big step up from just using a password, which can sometimes be guessed or stolen. With an SSH key, you're relying on a very long, complex code that's practically impossible to guess. And because it's a two-part system, even if someone somehow got hold of the public key, it's useless without the private one. This makes it a much more robust way to protect your remote IoT platform's access to its devices. You're building a very strong fence around your digital property, so to speak. This means your data stays private, your commands are truly yours, and your devices do exactly what they are supposed to do, and nothing else. It’s pretty much a digital bodyguard for your device communications, which is a good thing, really.
How Does a remoteiot platform ssh key Actually Work?
Let's get a little more specific about how this digital magic happens. When you want your remote IoT platform to connect to one of your devices, the process isn't just a simple login. It's more like a secret conversation where both sides prove who they are without ever giving away their deepest secrets. The platform says, "Hey, it's me!" and the device says, "Prove it!" Then, using the public and private keys, they exchange some encrypted information. It’s a back-and-forth, a kind of challenge and response, until both sides are absolutely sure they are talking to the right party. Only then does the actual communication begin. This whole process happens super fast, so you probably won't even notice it, but it's happening every time your platform needs to reach out to a device. It's pretty cool, if you think about it, how much happens in the background, just like that.
The Handshake Behind the remoteiot platform ssh key
Think of it as a very polite, very secure introduction. Your remote IoT platform holds one half of a unique key pair – the private part. The IoT device you want to talk to holds the other half – the public part. When the platform tries to connect, the device sends a random piece of data. The platform then uses its private key to "sign" this data, proving it has the correct private key, and sends it back. The device, using the public key it has, checks that signature. If the signature matches, the device knows it's the legitimate platform trying to connect. This means that the private key never travels across the internet, which is a huge security plus. It stays put, safe and sound, on your remote IoT platform. This method is incredibly secure, which is why it's a widely trusted way to manage access, more or less, for pretty much any kind of remote system.
Setting Up Your remoteiot platform ssh key - Is It Hard?
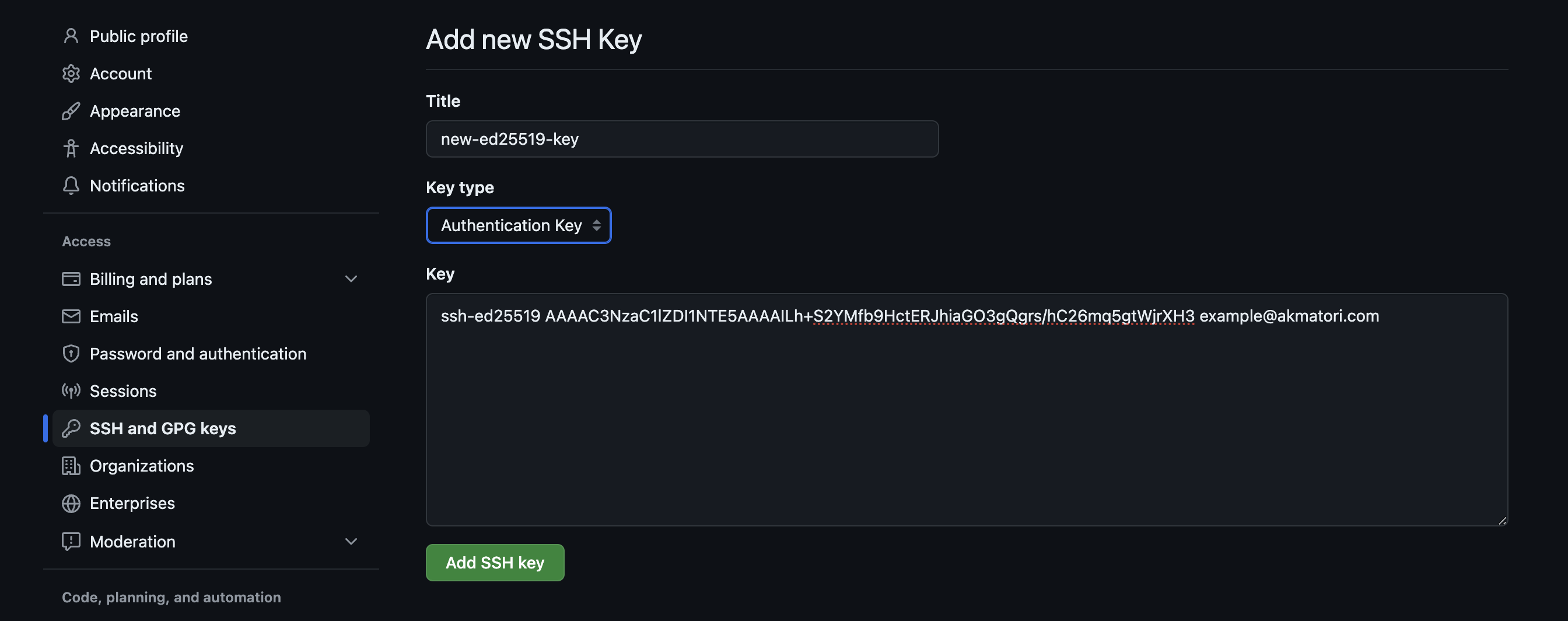
The idea of setting up security keys might sound a bit intimidating at first, especially if you're not used to working with these kinds of things. But honestly, for most remote IoT platforms, the process has been made quite straightforward. You typically generate your key pair on your computer or directly within the platform's interface. Then, you copy the public part of that key to your IoT devices. The steps usually involve just a few commands or clicks. Many platforms have guides that walk you through it, step by step, so you're not left guessing. It’s a bit like setting up a new app on your phone; there are steps to follow, and once you do it once or twice, it becomes much easier. It's not nearly as complicated as it might seem, so, really, don't let the name scare you off.
Steps to Get Your remoteiot platform ssh key Going
Generally speaking, the process for getting your remote IoT platform SSH key working involves a few main actions. First, you'll create the key pair on your main system or the server where your platform lives. This creates both the public and private parts. Next, you'll need to get the public key onto each of your IoT devices. This might mean logging into each device once with a temporary password or using a setup script. Once the public key is on the device, you can usually disable password logins, making the SSH key the only way in. This dramatically reduces the chances of someone guessing their way into your devices. Finally, you'll configure your remote IoT platform to use your private key when it wants to talk to those devices. It's a pretty standard procedure, and most systems are set up to make it as simple as possible, you know, for everyone.
What If Your remoteiot platform ssh key Doesn't Behave?
Sometimes, even with the best intentions, things don't work perfectly the first time. If your remote IoT platform isn't connecting to your devices using the SSH key, there are a few usual suspects. It could be that the public key wasn't copied correctly to the device, or maybe there's a tiny typo in the key itself. Sometimes, the permissions on the key files aren't set right, which means the system can't read them properly. Or perhaps, the private key isn't stored in the exact spot your platform expects it to be. It's a bit like trying to open a door with the right key, but you're holding it upside down. These are usually small things that are easy to fix once you know what to look for. Don't worry too much, as a matter of fact, these little issues happen to everyone.
Common Hiccups with Your remoteiot platform ssh key
When you run into trouble with your remote IoT platform SSH key, a good first step is to double-check that the public key on the device is an exact copy of the one generated. Any extra spaces or missing characters can cause problems. Also, make sure the private key on your platform's side is accessible and has the right permissions – typically, only you should be able to read it. Firewalls, both on your platform's side and the device's side, can also block connections, so checking those settings is always a good idea. Sometimes, the problem is just a simple oversight, like forgetting to restart a service after making changes. Patience and a systematic check usually sort things out pretty quickly. It's pretty much a process of elimination, really, until you find that one small thing that's out of place.
The Good Stuff - What a remoteiot platform ssh key Brings You
So, why go through all this for a remote IoT platform SSH key? Well, the biggest benefit is the immense peace of mind it offers. Knowing that your devices are communicating securely, and that only authorized systems can access them, takes a huge load off your shoulders. It means you can focus on what your IoT system is supposed to do – collecting data, automating tasks, improving efficiency – instead of constantly worrying about potential security breaches. It also makes managing many devices much simpler. You don't have to remember different passwords for each one; the key pair handles the authentication for you. This kind of security isn't just about keeping bad guys out; it's also about making your life easier and your operations smoother. It's a pretty good deal, honestly, when you think about it.
Peace of Mind with Your remoteiot platform ssh key
Beyond just security, using an SSH key with your remote IoT platform offers practical advantages. It streamlines the process of connecting to and managing your devices. Once set up, you can automate many tasks, like software updates or data retrieval, knowing that the connection is always authenticated and secure. This saves time and reduces the chance of human error. It also provides a clear audit trail; if something goes wrong, you can trace who or what accessed the device. For anyone serious about deploying IoT devices, whether for personal projects or large-scale industrial uses, adopting SSH keys is just a smart move. It's about building a solid foundation for your connected future, you know, making sure everything runs smoothly and safely.
Looking Ahead - The Role of Your remoteiot platform ssh key
As more and more devices connect to the internet, and as our lives become more intertwined with these smart systems, the need for strong security will only grow. The principles behind the remote IoT platform SSH key are timeless and will continue to be a cornerstone of secure remote access. We'll likely see even simpler ways to manage these keys and integrate them into platforms, making it even easier for everyone to use them. The focus will remain on making security something that's built-in and effortless, rather than an afterthought. So, learning about and using SSH keys now puts you in a good spot for whatever comes next in the world of connected things. It's pretty much a foundational skill, in a way, for anyone playing with IoT.
The Future of Your remoteiot platform ssh key
The core idea of using a private and public key pair for authentication is really quite brilliant in its simplicity and effectiveness. It's a method that has stood the test of time in the computing world, and it's perfectly suited for the unique challenges of IoT. As remote IoT platforms become even more sophisticated, we can expect SSH key management to become even more automated and user-friendly. Perhaps there will be new ways to recover lost keys or revoke compromised ones with even greater ease. But the underlying concept of strong, asymmetric cryptography will remain. It’s a very reliable way to keep your digital conversations private and your remote devices truly yours. So, honestly, understanding this bit of tech is a pretty useful thing.
Related Resources:

Detail Author:
- Name : Anthony Grimes MD
- Username : cameron.ward
- Email : rwalker@stroman.org
- Birthdate : 1973-11-20
- Address : 9111 Jerde Pike East Mazieside, OR 24873
- Phone : 305.341.9025
- Company : Gleason, Senger and Feeney
- Job : Electrical Engineering Technician
- Bio : Ut consequuntur excepturi rem possimus. Quas sed vitae et aut fugit. Officia aliquam fugiat beatae est quo velit.
Socials
facebook:
- url : https://facebook.com/lindc
- username : lindc
- bio : Odit blanditiis delectus quidem architecto mollitia voluptates voluptate harum.
- followers : 2178
- following : 599
tiktok:
- url : https://tiktok.com/@cesar_lind
- username : cesar_lind
- bio : Labore vel nam voluptatem voluptatem ducimus optio alias.
- followers : 4168
- following : 925